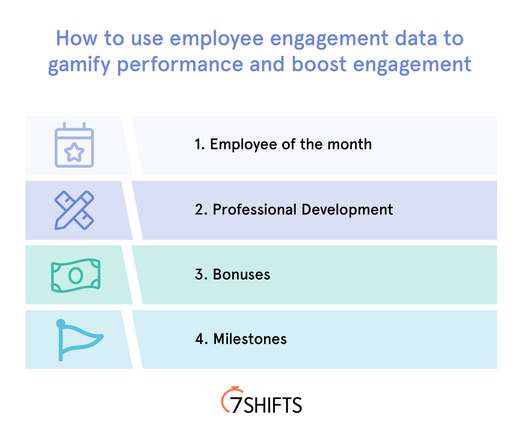
What Restaurateurs Need to Know about Third-Party Cybersecurity Risks
Modern Restaurant Management
MAY 23, 2025
First, bad actors gain unauthorized access to your POS vendor’s development environment, perhaps by exploiting known security vulnerabilities or using phishing tactics to steal employees’ login credentials. Request proof of security certifications and compliance with industry regulations.















































Let's personalize your content