Cell Phone Policy At Work: Downloadable Template
Cell phones and mobile devices are an integral part of our personal and professi...

If your business is going to allow team members to use their personal phones, tablets, and laptops to access private networks, data, and apps, it will absolutely need a BYOD policy.
Without such a policy in place, you open your business up to all manner of serious security threats.
In this article, we discuss the concept and practice of BYOD and give you tips for creating a policy that keeps your business data safe and secure.
BYOD is an abbreviation (or, more specifically, an initialism) for the phrase Bring Your Own Device.
BYOD refers to the practice of allowing employees to use their personal devices — be they anything from smartphones to desktops to simple USB drives — to access business networks, work-related systems, and sensitive or confidential data.
As more and more businesses incorporate work-from-home and remote-work options for their employees, BYOD solutions are becoming more prevalent and more important.
As the popularity of BYOD practices grows, so too does the necessity of policies to govern what team members can and cannot do with their personal device while connected to your business network.

A BYOD policy is a set of rules, regulations, and guidelines that defines acceptable and unacceptable use of the company network while on a personal device.
An effective BYOD policy is about more than just what types of websites employees can access.
Comprehensive policies even go so far as to define who has access to what information, which devices are allowed on the system, and where employees can store data.
Regardless of how detailed your BYOD policy might turn out to be, there are four basic options your IT department will have to contend with:
Each of these options comes with different risks and requires different policies to keep your data secure.

More and more employees feel that their personal devices are more effective and productive than those that the business provides.
Put simply, they would prefer to use their personal devices for work purposes.
That leaves businesses with two options:
Stated this way, it’s fairly obvious which of the two most businesses are adopting (the latter).
But where does a BYOD policy come into all this?
Such policies help businesses find a balance between managing risk (i.e., keeping business data secure) and improving productivity (i.e., making it easier for team members to focus on the daily job).

Don’t get behind the eight ball by implementing a BYOD practice before you create a BYOD policy.
When it comes to IT issues, policy must always precede technology.
When creating a bring-your-own-device policy, consider the following questions:
These are just a few of the important questions your business should ask when creating a BYOD policy.
When it comes to enrollment in your BYOD policy, complexity breeds non-compliance.
Make enrollment and rollout simple so that users can, in essence, download a business profile and self-configure their device(s) according to company standards.
The more automated the enrollment process, the better (for end-users and IT personnel alike).
In the same way that you want to automate enrollment and rollout, your BYOD policy should automate common help issues.
For example, let users directly perform such tasks as:
Automating common help issues such as this will free up time for your IT department and help them optimize their activities.

An effective BYOD policy protects your business’s privacy and the security of its data.
But an effective BYOD policy also protects the privacy of its users’ personal information — from outside eyes as well those inside the business.
That means that any solutions you implement are restricted from accessing such things as:
When creating a BYOD policy, be sure to let users know what you do and do not collect, how it will be used, and why you are collecting the things you do.
A big part of any BYOD policy is what constitutes personal data and what constitutes corporate data.
When you define that, you also want to define how you will keep the two separate.
For example, if an employee decides to leave your company, your BYOD policy states that corporate apps, documents, and other business material are protected by IT and will be remotely deleted, while personal email, photos, and apps will go untouched.
Another big part of a robust BYOD policy is how your business will monitor devices for noncompliance.
Many IT systems offer automated solutions to the varying degrees of noncompliance, including:
However you choose to deal with “offenses” that go against your BYOD policy, monitoring devices for noncompliance will be a big part of what your IT department does on a regular basis.
As we mentioned in the first tip on this list, your business will need to decide how it’s going to manage the data used by all the new devices.
You can simplify the process by paying for the data yourself, but you’ll still want a way to track who is using what and control things so that costs don’t affect your bottom line.
BYOD practices and policies have flourished in the past decade as businesses of all types and sizes recognize the benefits of remote work.
Along with the new realization that flexible is better comes the reality that allowing employees to bring their own devices is another way to cut costs and allow the business to funnel funds to other activities and growth opportunities.
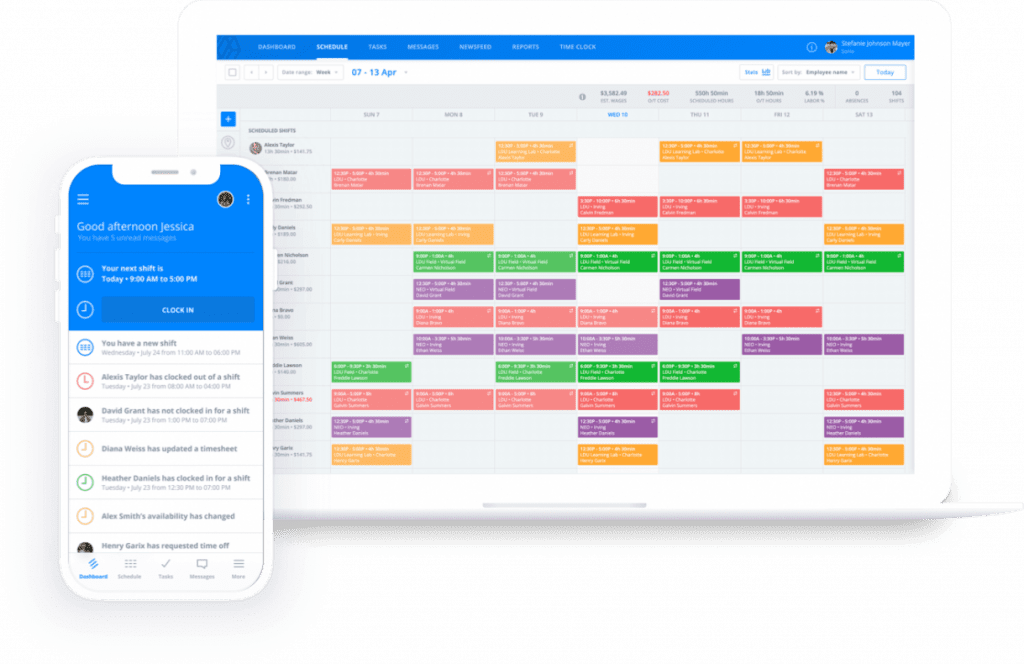
This flexibility behind BYOD practices and policies — and the benefits it provides — even extends into the realm of employee scheduling where things can get complicated very quickly.
Computer software simplifies the job, but it comes with a caveat: you’ve got to use the right software.
Scheduling five, ten, 20, or 100+ employees with anything other than the best workforce optimization software — with Sling — makes the job even more difficult than it would be without the software.
The Sling suite of tools is perfect for creating even the most difficult types of schedules because it offers features that other programs don’t.
Features of the Sling app include:
The Sling app even incorporates onboard artificial intelligence that warns you when conflicts arise and then suggests solutions.
Try Sling for free to discover the myriad ways it can help streamline the way you schedule around the gig economy and how it can take your business to the next level.
For more free resources to help you manage your business better, organize and schedule your team, and track and calculate labor costs, visit GetSling.com today.
See Here For Last Updated Dates: Link
This content is for informational purposes and is not intended as legal, tax, HR, or any other professional advice. Please contact an attorney or other professional for specific advice.
Schedule faster, communicate better, get things done.